FAQ
- The subscriber’s name and other unique identification information e.g. NRIC, passport number etc.
- The subscriber’s public key
- Name and digital signature of the issuing Certificate Authority
- Expiry date of the certificate.A corporate Netrust Digital Certificate will contain the same information as for the “individual certificate” with the following additional fields:
- Industry group name (optional)
- Organisation name
- Organisation unit/s (if applicable)
The cost of re-issuing the certificate is S$10.80 (inclusive of 8% GST).
Who to contact for enquiries or help?
- Netrust Customer Service Hotline: +65 6212 1388 (please leave a voicemail, if necessary)
- Email: infoline@netrust.net
- Website: https://www.netrust.net/contact-us
- must be at least 8 characters long;
- must be less than or equal to 16 characters long;
- must contain an uppercase character;
- must contain a lowercase character;
To proceed with an online remote session, please take note that there is an additional courier fee of $18 (inclusive of 8% GST) for the delivery of the token.
Cost for replacement of cryptographic token is as follows:
| S/No | Item | Prices |
| 1. | Administrative Fee | $10 (one-time cost) |
| 2. | Cryptographic Token | $100 |
Who to contact for enquiries or help?
- Netrust Customer Service Hotline: +65 6212 1388 (please leave a voicemail, if necessary)
- Email: infoline@netrust.net
- Website: https://www.netrust.net/contact-us
Who to contact for enquiries or help?
- Netrust Customer Service Hotline: +65 6212 1388 (please leave a voicemail, if necessary)
- Email: infoline@netrust.net
- Website: https://www.netrust.net/contact-us
Where do I register for a Netrust Digital Certificate?
Please send an email to infoline@netrust.net to request for the application form and understand more about the cost and documents required for this process.
Upon completion of generating the certificate, applicants will be notified via email to proceed to Netrust office for the collection.
What types of Netrust Digital Certificates are available and what are the differences?
There are two (2) types of Netrust Digital Certificates, namely
- Corporate Net-ID Certificate; and
- Personal Net-ID Certificate.
Corporate Net-ID Certificate:
- The certificate bears the name of the firm/company of the applicant;
- Future annual subscription billing for the Netrust Digital Certificate will be addressed to the firm/company; &
- Netrust’s liability limit – Singapore Dollars Eighty Thousand (S$80,000.00).
Personal Net-ID Certificate:
- The certificate does not bear the name of the firm/company of the applicant;
- Future annual subscription billing for the digital certificate will be addressed to the applicant; &
- Netrust’s liability limit – Singapore Dollars Ten Thousand (S$10,000.00)
What do I have to submit to register for a Netrust (Net-ID) Digital Certificate?
For applicant applying for Personal Net-ID Certificate, please email item 1 to 3 in a .zip file, password protected. For applicant applying for Corporate Net-ID Certificate, kindly email item 1 to 5 in a .zip file, password protected.
- Copy of the identification document of Applicant – NRIC/Passport or Work Permit (for foreigners) – *Driving License will not be accepted
- Practicing Certificate
- Netrust Digital Certificate Application Form
(download Interactive Corporate Net-ID Application Form here)
(download Interactive Personal Net-ID Application Form here) - Letter of Authorization, authorizing the Applicant to apply for the token (see Sample Letter);
NOTE : This letter does not permit a proxy to come on behalf of the applicants. - Copy of Business Profile/ACRA (must be generated within the year of application)
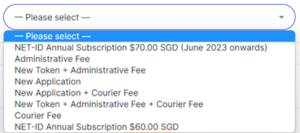
How much do I have to pay?
| S/No | Items | Prices |
| 1 | Netrust Digital Certificate (Corporate and Personal) | $70 (renewable annually) |
| 2 | Registration Fee | $10 (one-time cost) |
| 3 | Cryptographic Token | $100 |
Mode of payment (upon collection):
- Cash
- Cheque (made payable to Netrust Pte Ltd)
- NETS
- Visa
- Mastercard
- PayNow
What operating systems are supported by Netrust software?
Supported platforms:
- Windows 8
- Windows 10
- Windows 11
The certificate has a lifespan of 3 years from the date of issue. Netrust Digital Certificate renewal can be done online using the Entrust Entelligence Security Provider (EESP). A dedicated update prompt will appear on the right hand side of the taskbar on the 30th to the 36th month of the certificate validity.
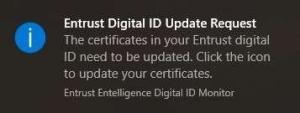
Click on the icon and user’s information will display. Select “Update” to proceed with the Netrust Certificate Update. Once successful, the token validity will be extended to 3 years from the date of the update.
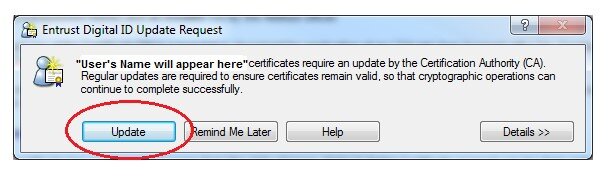
Should your certificate become invalid due to failure to update your certificate online, please contact Netrust Customer Service to assist for a certificate recovery. This service is chargeable as stated in the Netrust FAQ.
Who to contact for enquiries or help?
- Netrust Customer Service Hotline: +65 6212 1388 (please leave a voicemail, if necessary)
- Email: infoline@netrust.net
- Website: https://www.netrust.net/contact-us
Please send an email to infoline@netrust.net to request for the application form and understand more about the cost and documents required for this process.
Upon completion of generating the certificate, applicants will be notified via email to proceed to Netrust office for the collection.
What do I have to submit to register for a Netrust (Net-ID) Digital Certificate?
Please check the pre-requisites for the application you would like to proceed with and email the required documents in a .zip file, password protected.
Pre-requisites (Corporate Net-ID Application)
- Corporate Net-ID Interactive Application Form
- Letter of Authorization, authorizing the Applicant to apply for the token under their Company. The Letter must be printed on the Company Letterhead.
- Original or Certified True Copy of the Practicing Cert (Issued By Board of Architects, Professional Engineers Board, Public Utilities Board)
- Copy of Business Profile/ACRA (Must be generated within the year of application)
- Copy of the Identification document of Applicant – NRIC/Passport or Work Permit (foreigners) – *Driving License will not be accepted
- Personal Net-ID Interactive Application Form
- Original or Certified True Copy of the Practicing Cert (Issued By Board of Architects, Professional Engineers Board, Public Utilities Board)
- Copy of the Identification document of Applicant – NRIC/Passport or Work Permit (foreigners) – *Driving License will not be accepted
- Corporate Net-ID Interactive Application Form
- Letter of Authorization, authorizing the Applicant to apply for the token under their Company. The Letter must be printed on the Company Letterhead.
- Builder’s License letter / Update of Builder Key Personnel letter issued by BCA
- Copy of Business Profile/ACRA (Must be generated within the year of application)
- Copy of the Identification document of Applicant – NRIC/Passport or Work Permit (foreigners) – *Driving License will not be accepted
- Personal Net-ID Interactive Application Form
- Builder’s License letter / Update of Builder Key Personnel letter issued by BCA
- Copy of the Identification document of Applicant – NRIC/Passport or Work Permit (foreigners) – *Driving License will not be accepted
- Personal Net-ID Interactive Application Form
- Certificate of Registration (Issued By BCA)
- Copy of the Identification document of Applicant – NRIC/Passport or Work Permit (foreigners) – *Driving License will not be accepted
| Item | Price(SGD) |
| 1. Netrust Digital Certificate (renewable annually) : | $70 |
| 2. Registration Fee (one-time cost) : | $10 |
| 3. Cryptographic Token: | $100 |
| 4. GST (8%) : | $14.40 |
| TOTAL | $194.40 |
- Cash
- Cheque (made payable to Netrust Pte Ltd)
- NETS
- Visa
- Mastercard
- PayNow
What operating systems are supported by Netrust software?
Supported platforms:
- Windows 8
- Windows 10
- Windows 11
Lifespan of Certificate
The certificate has a lifespan of 3 years from the date of issue. Netrust Digital Certificate renewal can be done online using the Entrust Entelligence Security Provider (EESP). A dedicated update prompt will appear on the right hand side of the taskbar on the 30th to the 36th month of the certificate validity.


Click on the icon and user’s information will display. Select “Update” to proceed with the Netrust Certificate Update. Once successful, the token validity will be extended to 3 years from the date of the update.

Should your certificate become invalid due to failure to update your certificate online, please contact Netrust Customer Service to assist for a certificate recovery. This service is chargeable as stated in the Netrust FAQ.
Who to contact for enquiries or help?
- Netrust Customer Service Hotline: +65 6212 1388 (please leave a voicemail, if necessary)
- Email: infoline@netrust.net
- Website: https://www.netrust.net/contact-us
Please send an email to infoline@netrust.net to request for the application form and understand more about the cost and documents required for this process.
Upon completion of generating the certificate, applicants will be notified via email to proceed to Netrust office for the collection.
Which type of Netrust Digital Certificate should I apply for?
You will obtain a Netrust Corporate Net-ID Certificate with the following information:
- The digital certificate would bear the name and masked NRIC number of the User;
- User shall be accountable for the certificate; and
- Future billing for digital certificate subscription renewal would be addressed to the User, unless otherwise specified
Please email the following required documents in a .zip file, password protected.
- Copy of the Identification document – NRIC/ Passport or Work Permit (for foreigners) – *Driving License will not be accepted
- Netrust Digital Certificate Interactive Application Form
(download Interactive Corporate Net-ID Application Form here) - Letter of Authorisation (LOA Template Link) (printed on the company Letterhead). ALL Application submitted to Netrust must include a Letter of Authorization. Netrust token application will not be processed if this document is not submitted to Netrust.
- Copy of Business Profile/ACRA (Must be generated within the year of application)
- Copy of the Approval Email / completed and signed SA01 Form sent by LTA to the user stating the approval of company / ESA
| S/N | ITEM | PRICE (SGD) |
| 1. | Netrust Corporate Net-ID Certificate (annual fee) | $70 |
| 2. | Registration fee | $10 |
| 3. | Cryptographic Token | $100 |
| Total | $180 |
Modes of payment (upon collection):
- Cash
- Cheque (made payable to Netrust Pte Ltd)
- NETS
- Visa
- Mastercard
- PayNow
Which Operating Systems are supported by Netrust software?
Supported platforms:
- Windows 8
- Windows 10
- Windows 11
The certificate has a lifespan of 3 years from the date of issue. Netrust Digital Certificate renewal can be done online using the Entrust Entelligence Security Provider (EESP). A dedicated update prompt will appear on the right hand side of the taskbar on the 30th to the 36th month of the certificate validity.


Click on the icon and user’s information will display. Select “Update” to proceed with the Netrust Certificate Update. Once successful, the token validity will be extended to 3 years from the date of the update.

Should your certificate become invalid due to failure to update your certificate online, please contact Netrust Customer Service to assist for a certificate recovery. This service is chargeable as stated in the Netrust FAQ.
Who to contact for enquiries or help?
- Netrust Customer Service Hotline: +65 6212 1388 (please leave a voicemail, if necessary)
- Email: infoline@netrust.net
- Website: https://www.netrust.net/contact-us
- Quick Buying Guide for Netrust Myinfo Certificate
- Quick Buying Guide for Netrust SafeEntry Certificate
- Quick Buying Guide for Netrust Server to Server Authentication Certificate
- Quick Buying Guide for nSignBasic Document Signing Certificate (Individual)
- Quick Buying Guide for nSignBasic Document Signing Certificate (Organisation)