Public Key Infrastructure (PKI) Explained
What is Public Key Infrastructure (PKI)?

What are the five main components of PKI?

1. Key Pairs:
The foundation of Public Key Infrastructure (PKI) is the asymmetric cryptographic key pair, which includes a public key and a private key. The public key can be shared with anyone, while the private key remains confidential. Data encrypted with one key can only be decrypted with the other key.
2. Digital Certificates:
These act like digital ID cards and bind a public key to an individual/entity. Issued by a Certificate Authority (CA), they verify that the public key belongs to the person or entity named in the certificate.
3. Certificate Authorities (CAs):
CAs are trusted organizations responsible for issuing and managing digital certificates. Before handing out a certificate, the CA must authenticate the identity of the requester.
4. Registration Authorities (RAs):
RAs serve as verifiers for the CAs before a digital certificate is given to the end user. They accept requests for digital certificates and confirm the individual’s identity before the CA issues the certificate.
5. Certificate Revocation Lists (CRLs):
These lists comprise certificates revoked by the CA before their expiration date.
How Does PKI Work in a Typical Scenario?
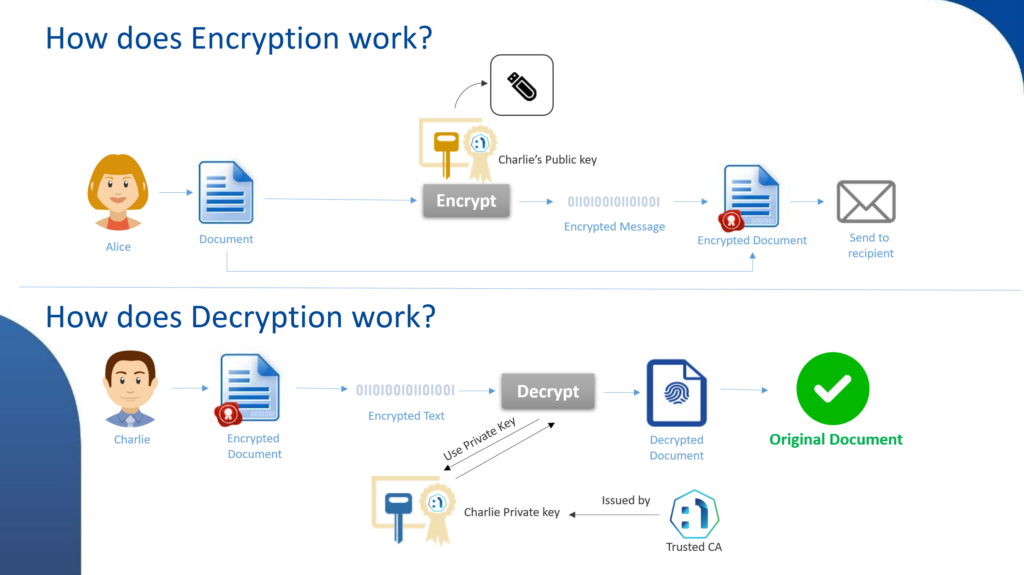
- Alice wishes to send Bob a confidential message. She encrypts the message using Bob’s public key.
- Bob gets the message. Using his private key, he decrypts it, guaranteeing confidentiality since only he possesses his private key.
- To verify the message’s integrity and authenticity, Alice can digitally sign the message with her private key. Bob can then validate the signature with Alice’s public key.
Benefits of Public Key Infrastructure (PKI)

Authentication:
Confirms the identity of parties in a communication.
Integrity:
Assures that a message hasn’t been tampered with during transmission.
Confidentiality:
Encrypts data so that only the intended recipient can view it.
Non-repudiation:
Proves a specific action taken by a user, making it challenging for them to deny it later.
Check out more information here: Netrust PKI Solutions
Why is Public Key Infrastructure (PKI) so important in today’s digital age?

-
Verifying Identity:
- Simple: Just like you check someone’s ID card, PKI checks digital IDs to make sure a website is genuine.
- Technical: PKI utilizes digital certificates, which are verified by Certificate Authorities (CAs), to establish the identity of entities. These certificates bind public keys with identities and are used to encrypt information that only the intended recipient’s private key can decrypt.
-
Encrypting Data:
- Simple: PKI scrambles your messages into a secret code, similar to a secret language that only you and your friend understand.
- Technical: Encryption through PKI involves using a pair of keys (a public key and a private key) in algorithms to convert plain text into ciphertext. This ensures that only someone with the proper private key can decrypt and read the data, protecting it from unauthorized access.
-
Ensuring Data Integrity:
- Simple: PKI ensures that the message you send is exactly what the receiver reads, like a seal on a letter that shows if it’s been opened.
- Technical: Digital signatures, part of the PKI, are used to verify that a message or document has not been altered since it was signed. This is accomplished by creating a hash of the original content and then encrypting the hash with the sender’s private key.
-
Securing Communications:
- Simple: PKI helps create a private space for conversations online, keeping eavesdroppers out.
- Technical: Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols that provide secure communication over networks. PKI provides the certificates that authenticate the parties involved and encrypt the data transferred between them.
-
Securing Online Transactions:
- Simple: When you buy something on the internet, PKI puts a virtual padlock on your payment information.
- Technical: E-commerce transactions are protected using encryption provided by SSL/TLS certificates. This ensures that sensitive data like credit card numbers are only accessible to the authorized parties processing the payment.
-
Compliance with Regulations:
- Simple: PKI helps businesses play by the rules when it comes to keeping personal information safe.
- Technical: PKI enables organizations to comply with regulations like the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA) by providing strong encryption and authentication mechanisms.
-
Internet of Things (IoT) Security:
- Simple: PKI makes sure the smart devices you use, like fitness watches or home assistants, are secure to use.
- Technical: As IoT devices proliferate, PKI ensures the integrity and confidentiality of the communication between devices and management systems by assigning and managing digital certificates for each device.
-
Preventing Security Breaches:
- Simple: PKI works to keep the bad guys out, stopping them from stealing from you online.
- Technical: PKI mitigates the risk of various security threats, including Man-in-the-Middle (MitM) attacks and impersonation attacks, by providing a trustworthy layer of validation and encryption.
-
Secure Remote Access:
- Simple: PKI helps you safely connect to your office network from home, just like using a key to get into your office.
- Technical: For remote work environments, PKI secures Virtual Private Networks (VPNs) and other remote access technologies by ensuring that the connections are authenticated and the data transmitted is encrypted.
-
Protection Against Cyber Attacks:
- Simple: PKI acts as a superhero shield to protect your personal information from internet villains.
- Technical: PKI architectures are designed to defend against a wide range of cyber-attacks by using encryption to protect the confidentiality and integrity of data and ensure that it is accessible only to intended users.
Check out more information here: HTTP vs HTTPS. What’s the Difference?
Public Key Infrastructure (PKI) in the ASEAN (Association of Southeast Asian Nations) region
-
Government Initiatives:
Many ASEAN countries have implemented e-Government initiatives that use PKI for securing communications and transactions, and for authenticating identities in digital services provided by the government. This includes tax filing, e-voting, and other government-to-citizen services. -
Financial Services:
In the banking and finance sector, PKI is essential for securing online banking transactions, establishing secure connections between customers and banks, and in mobile banking applications for authentication and transaction signing. -
E-Commerce:
With the rapid growth of e-commerce in ASEAN countries, PKI provides a foundation for secure transactions, SSL/TLS for website security, and consumer protection in online shopping environments. -
Healthcare:
PKI is increasingly important in the healthcare sector for protecting patient data, ensuring the confidentiality and integrity of medical records, and for secure communication between various healthcare providers and stakeholders. -
Education:
Educational institutions are utilizing PKI for secure access to online resources, protection of intellectual property, and to ensure the integrity and authenticity of academic records and online testing. -
Telecommunications:
For telecom operators, PKI offers a means to secure the communications network infrastructure, authenticate users and devices, and protect the confidentiality of communication data. -
Cross-border Transactions:
ASEAN’s focus on economic integration has led to increased cross-border digital transactions. PKI enables these transactions to be secure and reliable, facilitating trade and commerce in the region. -
IoT Security:
With the expansion of the Internet of Things (IoT) in the ASEAN region, PKI provides a critical layer of security for device authentication and secure data transmission. -
Compliance and Regulatory Requirements:
ASEAN countries are gradually enforcing regulations and compliance requirements that mandate the use of digital signatures and encryption based on PKI, especially in sectors like finance, legal, and healthcare. -
Cybersecurity Initiatives:
PKI forms a part of the broader cybersecurity initiatives undertaken by various ASEAN countries to combat cyber threats, enhance national security, and protect critical infrastructure.
Read our blog on PKI here: The PKIs in Our Daily Life
Contact Us: General enquiries or free consultation


