Vulnerability remediation is often an uphill task for most organisations as they struggle to identify, prioritise and remediate them. In addition, due to the dynamic landscape in vulnerability discoveries by third party vendors. It has made it even more challenging for them to step into this massive area without causing them massive headaches or anxieties.
To add on to the complexity of the situation, many employees are currently working from home due to the pandemic situation, and their remote computers need to be proactively monitored and patched in this dynamic vulnerability landscape.
The factors above increase the urgency & stress for an organisation’s respective IT personnel to tune their patch management workflows to suit the pandemic situation overnight to protect their company’s assets and enforce their organisation’s security posture.
The Stages of Vulnerability Management
Before we do a deeper dive into proactive vulnerability remediation. Let’s take a brief walkthrough on the stages of vulnerability management cycle.
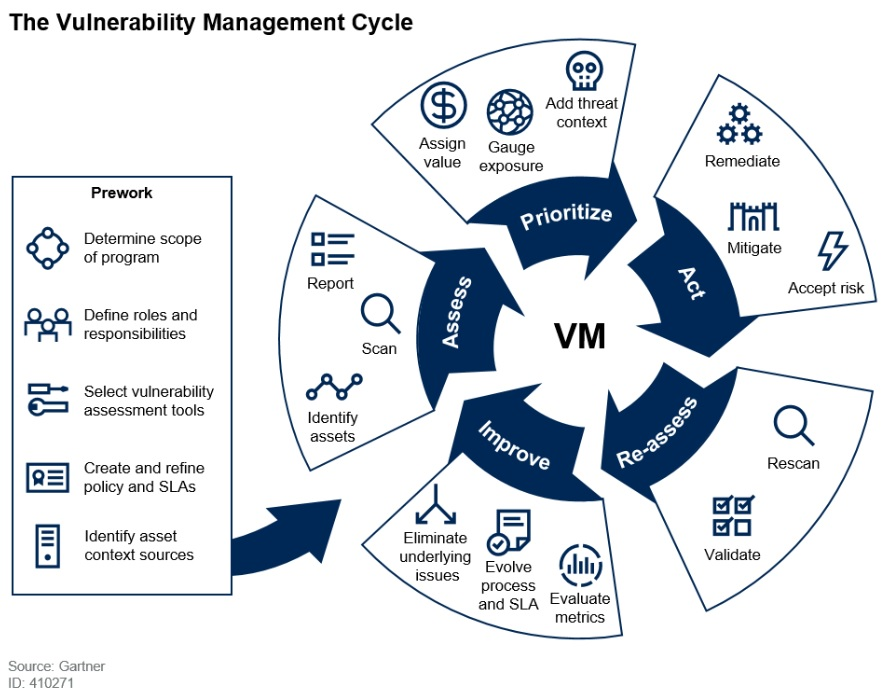
Vulnerability management is a process to identify, assess, prioritize, act, reassess & improve on your vulnerability management workflow to reduce the risk of cyber attack. This involves understanding vulnerabilities and staying up-to-date with the latest threats.
The process starts with an initial assessment, which helps determine the severity of the vulnerability and any potential impacts to assets or users. The assessment phase also determines if any mitigating controls are in place that could prevent or minimize any potential risks. If needed, a risk mitigation strategy can be implemented at this time, followed by an act or a decision about what should be done next for remediation.
Once the vulnerability has been remediated, we will then reassess the posture to ensure that the remediation has been properly administered by triggering a re-scan of the asset. To ensure that we improve the process, we will then reflect on the process to eliminate any underlying issues & help evolve it to enhance the SLA.
Proactive Vulnerability Remediation
Organizations are starting to recognize the need for proactive vulnerability remediation. It’s a way to reduce the risk of being compromised due to vulnerabilities in software and hardware. This proactive process also helps organizations move towards securing their mobile workforce during this pandemic or in future.
It is important to have knowledge on the tools & technology that will enable organisations to take the first step towards it. Patching has always been the center of vulnerability remediation, we have relied on third-party vendor patches to remediate any vulnerabilities affecting their products.
There are many tools out there that can achieve proactive vulnerability remediation. However, I would like to give a special mention to Qualys for their flexibility and ease of usage on vulnerability remediation using their Patch Management Module.
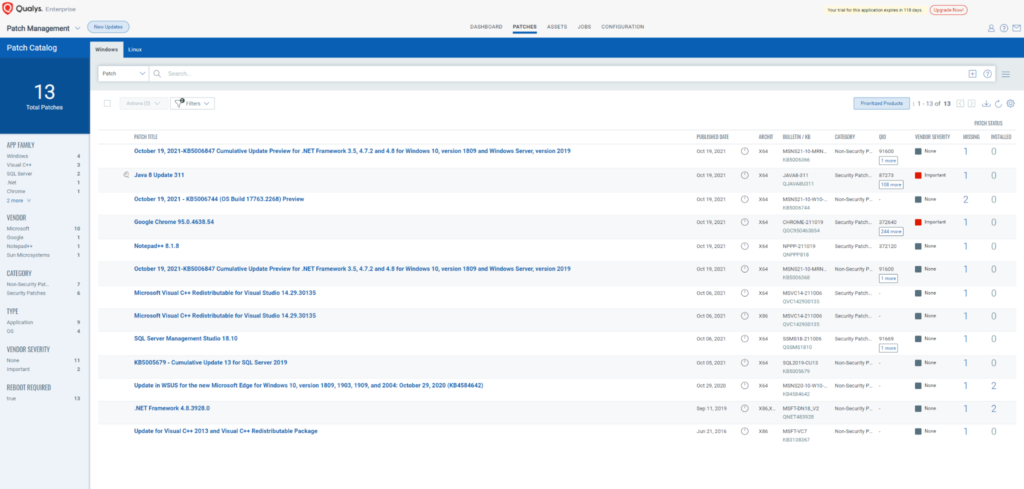
The beauty of Qualys is its ability to give you a cohesive dashboard on what patches are missing on each asset in an overview and it allows you to pivot directly to the asset to verify what patches are missing & it is able to allow users to filter the patches based on the respective products. Proactive vulnerability remediation using Qualys is fairly simple as patch deployment jobs can be created on a regular basis to allow organisations to take their first step towards proactive vulnerability remediation.
For organisations that want to start out small and within their acceptance risk level, the patch management module is able to target specific software for patching.
Smarter Patch Automation
Automating your proactive patch processes will save organisations time and effort. However, some considerations must be taken into account on which patch cycles should be automated based on their needs.
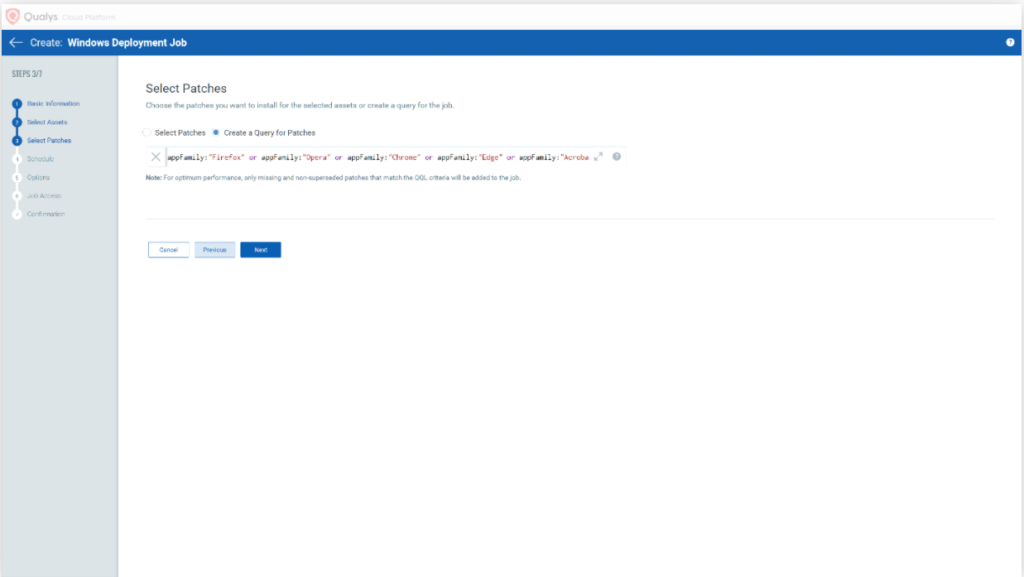
Qualys Patch Management offers organisations the flexibility to build their own patch management process. For example, an organisation can create a unique asset tag to target specific windows servers to deploy newly released patch Tuesday patches for their QA process to ensure that the patches are suitable for the applications before applying them to their production servers.
Deployment of patches can be chosen & selected, you can choose to deploy only newly released patches and third-party application patches or only deploy OS patches. This is highly customisable and can be fitted to any organisation’s need.
Taking the first step
Embarking on a proactive vulnerability remediation process may seem daunting at first. However, with the right technology and consultant, you will be well on your way to achieving it.
To get started, contact Netrust Sales Team at sales@netrust.net.


