In today’s Public Key Infrastructure (PKI) field, it is common to see organizations leverage on Microsoft Certificate Authority (CA) to build their internal PKI System. However, a lot of organizations are not aware of the security gaps that Microsoft brings to the table and what are the issues that might bring to them. In this blog, we will discuss the security gaps of Microsoft CA and how we can help to address them.
What is Microsoft Certificate Authority?
Microsoft CA’s official name is also known as Active Directory Certificate Services (ADCS). It is part of Windows Operating server features whereby the administrator can easily add the role of ADCS and enable the server to take up the role of a Certificate Authority.
Why do organizations choose to use Microsoft CA?
The distinct reason when it comes to choosing Microsoft CA would be the cost. As mentioned, ADCS is part of Windows server which means that once the organization has procured the Windows server license, they will be able to install the service.
There are also wide supports in the community that enable administrators on how to install ADCS step by step, making it easy to complete the installation.
Lastly, there are organizations or security personnel that do not know there are other alternatives to ADCS. This is not to be blamed as the cost and wide coverage and publicity of ADCS may overwhelm other enterprise grades CA in the industry.
Concerns with Microsoft CA…
There are multiple concerns that the free Microsoft CA fails to provide, for example, lack of multiple authorizations, leveraging on only AD credentials to access ADCS, Key escrow credentials and high availability.
However, the biggest gap that Microsoft CA fails to provide would be Certificate Life Cycle Management.
Today, ADCS is unable to keep track of the expiration of all the certificate that has been issued by the CA. In its very own native MMC snap-in console, the Administrator is unable to easily identify what are the certificate within its inventory and needless to say track the status.
At first glance, the lack of Certificate Life Cycle Management might seem to be an operative issue compared to security gaps. However, an organization must be aware that failure to keep the certificate in a valid status would be that services that use that certificate might potentially cause the provided service to be unavailable.
At the same time, the lack of tracking of certificates causes multiple certificates to be requested by application owners which means that multiple valid private keys may be residing somewhere in the system.
The truth today is that no organization hires a system administrator to handle the Microsoft CA within the organization. The assigned personnel will probably have their main job and are tasked to handle the CA portion as an added scope. With this, focus and expertise will not be present to handle the CA.
There are by no means that organization should stop using Microsoft CA for their internal PKI, but organization should be aware of the following security gaps that Microsoft CA possess and rectify them accordingly.
Solution to the security gaps
The base-level protection that all organization that uses Microsoft CA should adopt will be the discovery of all certificate issued within the organization and then provide notification on the status of the managed certificates.
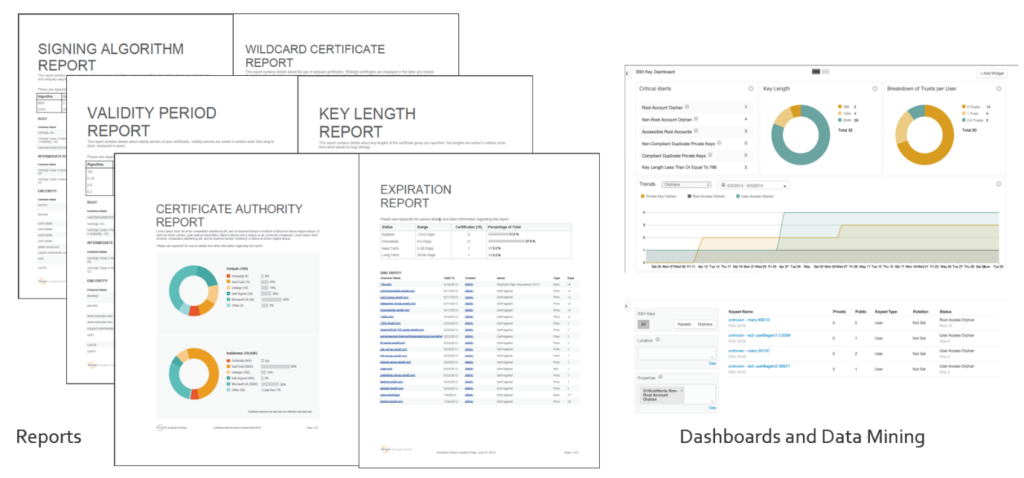
There are products that have a beautified dashboard that provides a bird eye view of all the certificates and provide critical information to an administrator at a glance.
Below are examples from certificate management products:
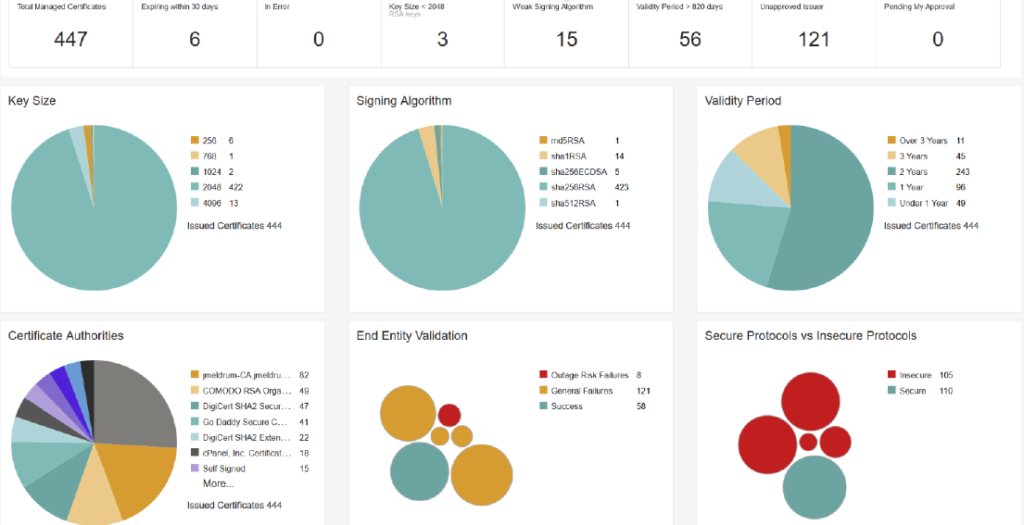
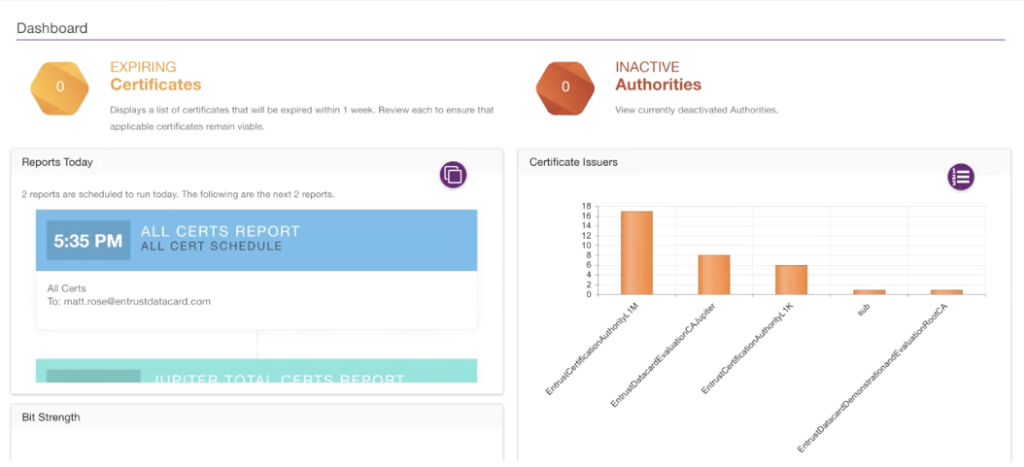
Solutions that are able to export reports and be able to automatically send them to the person-in-charge provides ease of management to keep track of the certificate. With a customizable report, Administrators are able to get information automatically without having to access the system daily.
Protect your organization today
Microsoft Certificate Authority will still be used ever so frequently in today’s organization given the benefits it brings to the table. An organization should adopt a third-party product that can help solve concerns that Microsoft CA is unable to provide.
Certificate management is critical and must be addressed.
If you have a Microsoft CA within your organization and find issues with it. Reach out to us and we can provide our consultancy to you and your organization.
To find out more, contact Netrust Sales Team at sales@netrust.net
Follow us on LinkedIn for the latest happenings/updates.


