Traditional security models, for example, Defence-in-depth security architectures have generally prioritized protecting the network perimeter. However, many of today’s breaches come from within enterprises, and these strategies are failing them. Zero trust is a strategic approach to cybersecurity by eliminating implicit trust and continuously validating every state of digital interaction. Zero Trust’s goal is to reduce the danger of cyberattacks in the modernized environments where the majority of enterprises work.
What is Zero Trust
Zero Trust Concept is a strategic approach to safeguard a business by removing implicit trust and constantly confirming each stage of a digital connection. The Zero Trust paradigm does not depend on a single piece of technology. Instead, the concept of “Zero Trust” refers to a set of technologies and best practices that are all geared toward reliably determining who is attempting to access or use data and whether they have explicit permission to do so. While most conventional approaches can be characterized as “trust but verify,” the principle underlying Zero Trust is frequently summarized as “never trust, always verify.”
Why Zero Trust
The main advantage of utilizing a Zero Trust strategy is security from all angles, especially from within. Defence-in-depth security architectures, for example, have historically centred protection on the network perimeter. However, many of today’s breaches come from within enterprises, and the traditional protection on network perimeter strategies is failing, anyone with network access has the potential to easily exfiltrate data. To combat this, Zero Trust prevents access from anybody and everyone until the network can be certain who you are. Then, it keeps track of how you’re using the data and may revoke your permission to copy if needed.
Approaching Zero Trust
There can be multiple approaches to the Zero Trust model, in this section I will be touching on the Forcepoint Remote Browser Isolation.
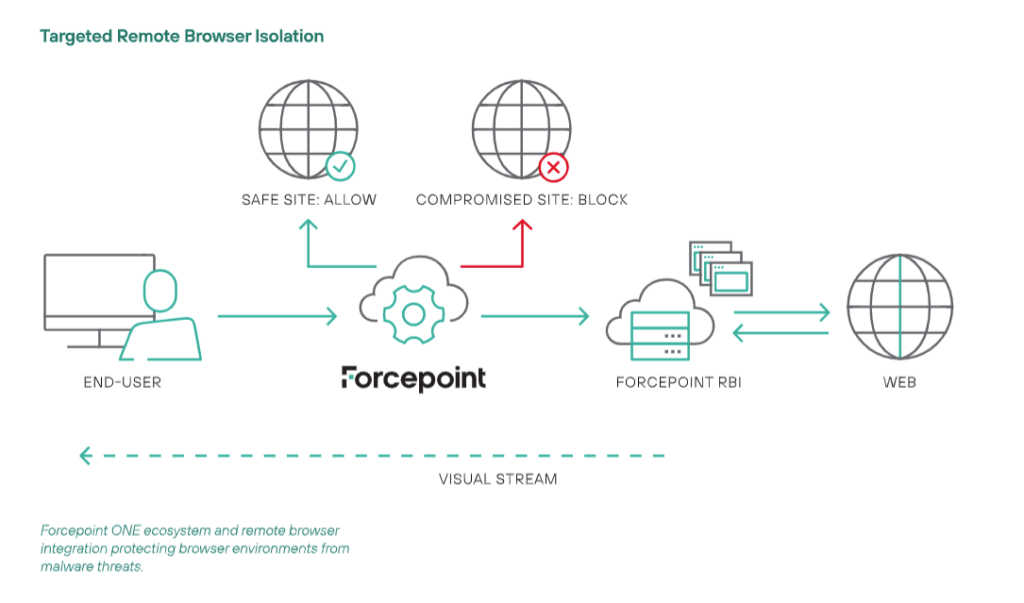
Forcepoint RBI
Delivery of malware via infected or malicious websites works because the user’s browser accepts and runs code from the site that the user visits. Remote Browser Isolation eliminates this in-browser code execution, protecting the user from malicious downloads in a sandboxed environment.
Forcepoint Remote Browser Isolation coupled with the Web Security Zero Trust Content Disarm and Reconstruction (CDR) technology doesn’t try to discern between good and bad; instead, it believes all data is hazardous or hostile. Web Security Zero Trust CDR extracts the business information from the documents and images in the web surfing stream and discards away any threat detected in the documents and images before the user is subsequently given access to entirely new documents and photos.
Benefits of Forcepoint RBI and CDR
1. Stop Malware Infiltration in Content
Adobe Portable Document Files and images are the most popular carrier of malware. These file formats are a prime target for attackers due to their complexity and the programs that use them. Regardless of the malware, they are using—from ransomware and banking Trojans to remote access kits and key loggers, cybercriminals are aware that the greatest spot to hide their most recent zero-day threat is inside a regular business paper. It is much more difficult to cope with the threat using traditional detection-based cyber security, and, with strategies like the use of file-less malware and file polymorphism the Web has become the ideal vector for infiltration.
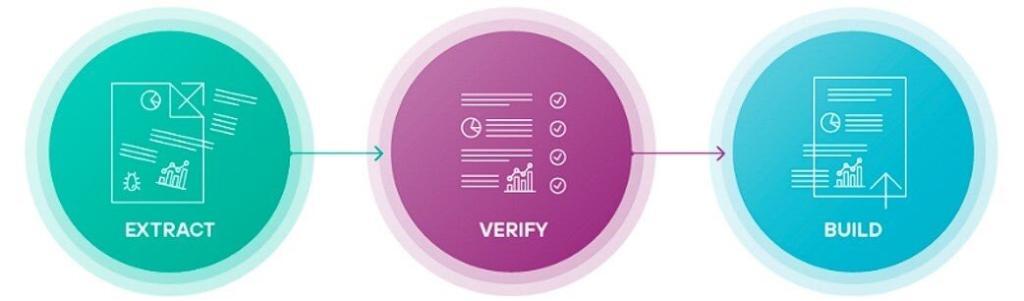
Zero Trust CDR for Web Gateways ensures that business users can upload and download business documents and images over the web with complete peace of mind because of the unique way they are transformed. Every document and image is subject to transformation and everyone is threat free.
2. Enrich the Browsing Experience
As security teams battle to deal with cyber attackers who seem able to constantly stay one step ahead, it is the business user who suffers. Business processes are slowed down, which reduces productivity. Time spent addressing false-positive security warnings or holding onto papers while they are reviewed and released, fixing these problems is expensive and time-consuming. Zero Trust CDR for Web Gateways improves the user’s web and social media experience by giving them quick access to the business information they need to read, share, and transact with zero chance of that content being compromised.
3. Transforming Your Web Security
Web Security Zero Trust CDR extracts the business information from the documents and images in the web surfing stream and discards away any threat detected in the documents and images before the user is subsequently given access to entirely new documents and photos. Zero Trust CDR does not allow any information to travel end-to-end. Attackers are unable to get in while the business gets what it needs. Zero Trust CDR ensures threats are removed from the content before the document reaches the end user.
Summary
With the rise of insider attack cases, traditional security model such as Defence-in-depth security architectures that focuses on protecting network perimeter is becoming abortive. Hence the need for the Zero Trust approach’s solution. Zero trust approach, is to adopt the never trust always verify mindset, focusing on the principle of least privilege, instead of the conventional trust but verify approach. With Forcepoint Web Security RBI, coupled with CDR, this solution can safeguard users. RBI can prevent any direct end-to-end transaction between users and servers. While CDR prevents any malware to be hidden in what seemed to be a typical file by disarming the malicious content and reconstructing back the file. All these benefits while being seamless to the end user.
Interested in achieving a continuous Zero Trust Model? Feel free to reach out to our Sales Team at sales@netrust.net or contact us on our website.
Follow us on LinkedIn for the latest happenings/updates.
Read more:


