The use of cloud technology has become a vital aspect of modern business operations, providing organizations with the ability to store, share, and access data from anywhere. However, with this convenience comes the risk of data breaches and cyber-attacks. To protect personal and business data in the cloud, it’s essential to implement robust security measures.
One of the key best practices for securing data in the cloud is to use a reputable cloud service provider. A well-established provider will have the resources and expertise to implement the latest security measures to protect your data. Additionally, they should also have a track record of security compliance, such as SOC 2, ISO 27001, and PCI DSS, which can provide added assurance that they are taking the necessary steps to protect your data.
Encryption is another critical aspect of cloud security. Encryption makes data unreadable to unauthorized parties and is essential for protecting data both in transit and at rest. To ensure that your data is secure, it’s important to use a robust encryption standard, such as AES-256.
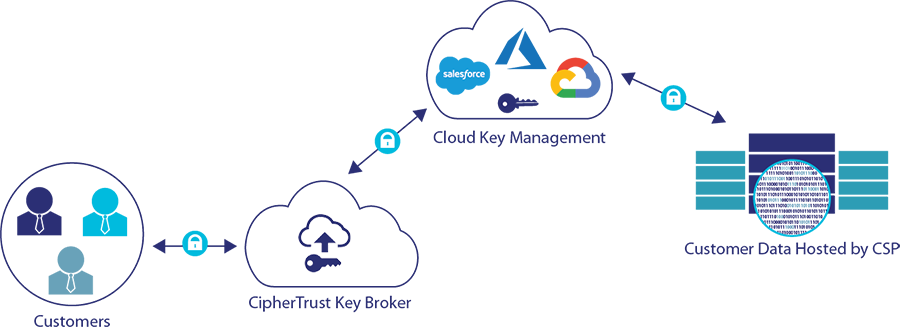
For organizations looking for greater control over their encryption keys, Thales offers a customer-managed key (CMK) solution. This allows customers to generate, store, and manage their encryption keys within their own infrastructure, rather than relying on a third-party provider. This gives customers greater control over their encryption keys and the ability to ensure that they are stored securely and compliant.
Strong authentication is also critical for protecting data in the cloud. Multi-factor authentication is one of the most effective ways to ensure that only authorized users can access your data. This requires users to provide multiple forms of identification, such as a password and a fingerprint or a security token, to access their accounts.
Controlling access to data is also crucial. Role-based access controls (RBAC) allow you to limit access to your cloud data to only those who need it. This can be implemented by creating different user roles and assigning different levels of access based on their job function.
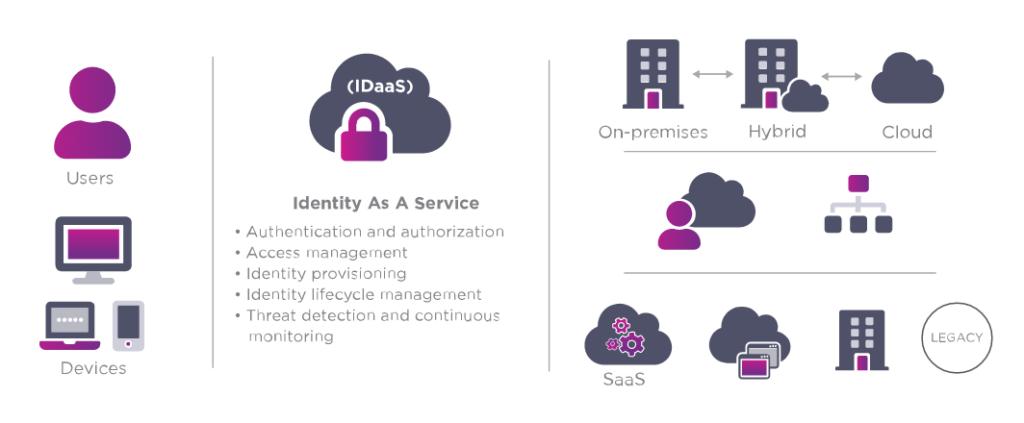
Entrust Identity-as-a-Service (IDaaS) is another solution that provides organizations with identity and access management (IAM) services. IDaaS solutions like Entrust offer a variety of features such as multi-factor authentication, single sign-on (SSO), access provisioning and de-provisioning, and identity governance. These features help organizations to secure their digital assets and meet compliance requirements. Additionally, Entrust IDaaS is scalable, flexible, and can be easily integrated with existing systems, making it an attractive solution for businesses of all sizes.
Regularly backing up your data is essential for protecting it in the cloud. Backing up data to a secure location ensures that you can restore it in case of a data breach or cyber-attack. This can be done by using cloud-based backup solutions or by replicating data to a secondary data centre.
Monitoring and auditing your cloud environment is also important. Regularly monitoring and auditing your cloud environment can help detect and alert you to any suspicious activity. This can be done through the use of security tools, such as security information and event management (SIEM) and intrusion detection systems (IDS).
In conclusion, securing personal and business data in the cloud requires a comprehensive approach that includes using a reputable cloud service provider, encryption, strong authentication, controlling access, regular backups, monitoring and auditing, and using solutions like Entrust IDaaS and Thales CMK. By implementing these best practices and solutions, organizations can protect their data from cyber-attacks and data breaches.
Looking to protect your organisation’s data from cyber-attacks and data breaches with robust security measures in place? Speak to our consultants today at sales@netrust.net or contact us via our website.
Follow us on LinkedIn for the latest happenings/updates.


