Guest Contributor, Charles Huang, Co-Founder & COO of Scantist
In today’s digital-first world, the line between application development and AI integration has vanished. While this fusion drives innovation, it also creates a complex and expanded attack surface. How can organizations protect their software without slowing down progress? The answer lies in a unified approach to application security. Traditional, siloed tools are no longer enough to manage the intertwined risks of open-source dependencies, code vulnerabilities, and the unique threats targeting AI models. A modern security strategy requires a holistic platform that provides end-to-end visibility and control.
Now that you know what a digital signature is, let’s fill in the remaining information you will need to know to work with it.
The Challenge: Why Traditional Security Falls Short
Many IT teams today are playing a constant game of catch-up. They use one tool for scanning open-source libraries (SCA), another for analyzing their own code (SAST), a third to protect their new AI features, and perhaps manual consultants for periodic penetration testing. This fragmented approach is like trying to assemble a car with four different sets of instructions—it’s inefficient, creates blind spots, and leaves critical connections unsecured. The reality is that a vulnerability in a third-party library can be exploited to poison an AI model, or a weak API can expose sensitive data through a generative AI chatbot.
This complexity leads to several common problems:
- Vulnerability Overload: Teams are flooded with alerts from multiple tools, with no clear way to prioritize what truly matters.
- Siloed Visibility: Security, development, and operations teams lack a shared understanding of risk across the application lifecycle.
- Emerging AI Threats: Traditional firewalls and scanners are not designed to detect prompt injection, model manipulation, or data leakage from Large Language Models (LLMs).
- Manual Bottlenecks: Periodic, manual security tests can’t keep pace with rapid development cycles, leaving new features exposed.
The Solution: A Three-Layered Security Strategy
To address these challenges effectively, organizations need an integrated platform that secures the entire digital ecosystem. This involves a three-layered approach that covers the software supply chain, the AI models themselves, and proactive threat discovery. Scantist delivers this through its unified suite of AI-driven solutions.
1. Secure Your Foundation: AppDefender for DevSecOps
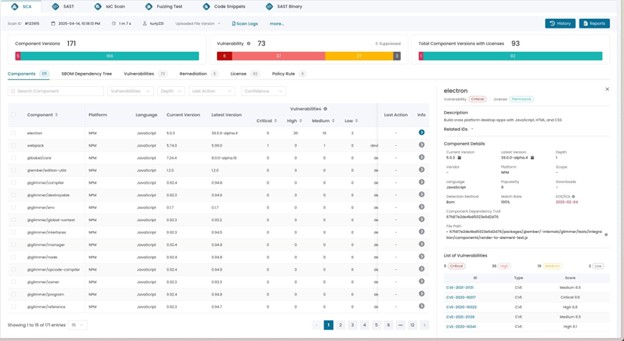
Everything starts with the code and its dependencies. Before you can secure your AI, you must secure the application it lives in. AppDefender, Scantist’s flagship DevSecOps platform, provides a solid foundation by securing your entire software supply chain.
- What it is: A comprehensive platform that combines Software Composition Analysis (SCA), Static Application Security Testing (SAST), and deep binary analysis.
- Why it matters: It gives you a single pane of glass to manage open-source governance, identify vulnerabilities in your own code, and ensure the integrity of your software from the first line of code to the final build. By automating DevSecOps orchestration and real-time SBOM management, it eliminates security noise and allows developers to focus on fixing what matters.
2. Protect Your AI: AIDefender for LLM Security
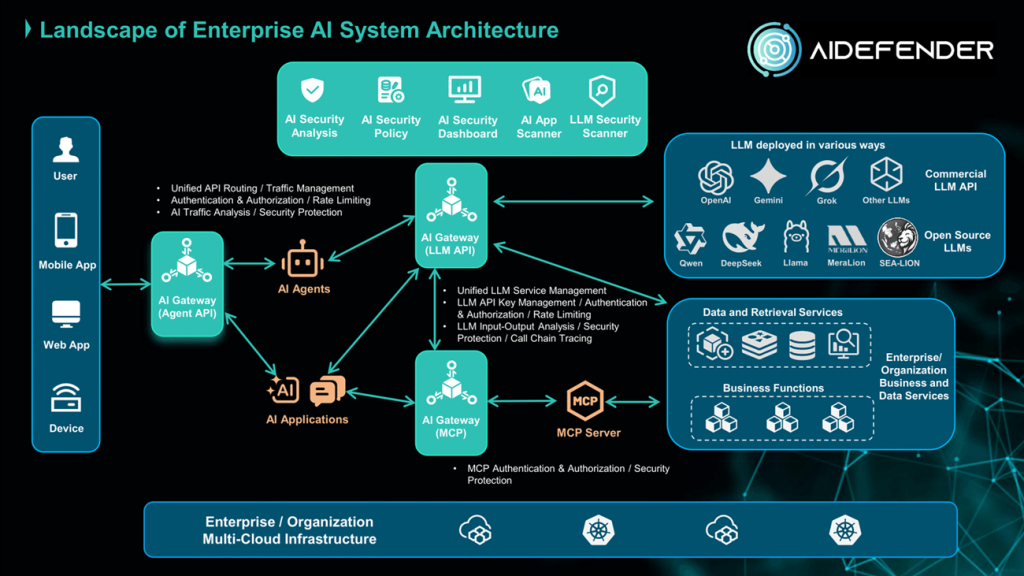
Once your application foundation is secure, the next layer is to protect the AI models and agents running on it. Generative AI introduces novel risks that require specialized defenses. AIDefender is purpose-built to be the security gateway for your enterprise AI.
- What it is: A dedicated AI security solution that protects against emerging threats targeting LLMs and generative AI tools.
- Why it matters: AIDefender prevents prompt injection attacks, detects and blocks sensitive data leakage, and monitors for model manipulation or poisoning. It ensures your AI implementations remain secure and compliant with evolving governance frameworks, allowing you to innovate with confidence.
3. Think Like an Attacker: PAIStrike for Automated Penetration Testing
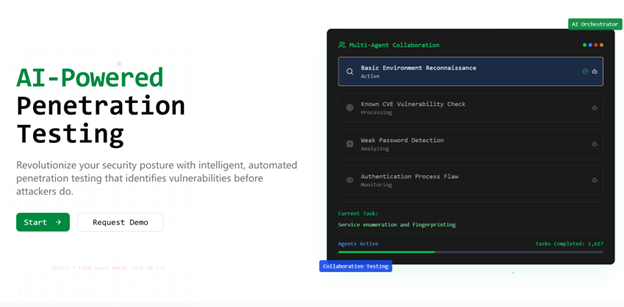
The final layer is to shift from a defensive posture to a proactive one. Instead of waiting for attackers to find your weaknesses, you need to find them first. PAIStrike revolutionizes this process with its automated, AI-powered penetration testing.
- What it is: An intelligent “red team” tool that uses multi-agent AI to automatically perform end-to-end penetration testing, just like a professional hacker.
- Why it matters: PAIStrike runs 24/7, continuously searching for vulnerabilities across your network, code, and infrastructure. It automates reconnaissance, vulnerability assessment, and exploit simulation, providing a true understanding of your security posture from an attacker’s perspective.
Best Practices for Holistic Security
Adopting these tools is the first step. To ensure lasting success, integrate them with a security-first mindset. Here are a few best practices:
- Shift Security Left, and Right: Integrate security checks early in the development process with AppDefender, but also continuously test your live environment with PAIStrike.
- Embrace Full-Stack Visibility: Use a unified platform to connect the dots between a vulnerability in a library, a risk in an AI model, and a potential exploit path.
- Automate Everything You Can: From SBOM generation to compliance reporting and penetration testing, automation frees up your team to focus on strategic risk reduction.
- Treat AI as a Unique Domain: Recognize that securing AI is not the same as securing a traditional application. Deploy specialized defenses like AIDefender.
Conclusion & Call to Action
In the age of AI, a fragmented security strategy is a losing one. Protecting your digital ecosystem requires a unified, intelligent, and proactive approach. By securing your software supply chain, protecting your AI implementations, and continuously testing your defenses, you can build true digital resilience.
Ready to simplify your security and focus on what matters? Contact Scantist today to learn how our unified platform can protect your applications and AI.


