Emails have become an essential part of our personal and professional lives and are used extensively in every organization. As a result, email is a popular attack for phishing and malware. Furthermore, email can be a conduit for the unintentional disclosure of sensitive data. Unfortunately, email infrastructure is less secure relative to other technologies, which is why email addresses can be spoofed and emails can appear to come from someone legitimate, in addition to this, email can still be sent in clear text, and on top of that email is not going away any time soon.
To protect information communicated via email, Secure/Multipurpose Internet Mail Extension (S/MIME) can help organizations in maintaining the authenticity of their email messages and reducing data breaches. S/MIME provides both digital identity and encryption that you can use to digitally sign and encrypt all your emails. S/MIME digitally signs your emails so that the recipient knows they came from you (and not someone pretending to be you). As the email travels from you to the recipient, encryption ensures that no unauthorized third party can access data.
Digitally signing and encrypting an email enables us to prove that the attachments and content originating from the sender’s email address haven’t been modified during transit.
Although standard encryption such as SMTP over TLS or STARTTLS helps to protect and protects data in motion, it isn’t really comparable to the security in S/MIME, which uses public key cryptography for end-to-end email encryption with data at rest.
How does S/MIME Secure Email
S/MIME is based on Public Key cryptography technology method that uses two asymmetric keys called a public key and a private key.
Encryption
S/MIME encryption allows the translation of information sent via email into an unreadable format. The encrypted email can only be decrypted or changed back into its original form by its intended recipient with a private key.
When you use Public Key cryptography to encrypt your emails, the email you send will be encrypted using the public key of the recipient. Without the corresponding private key, it is impossible to decrypt the email. The intended recipient of the email is the one who will possess the private key. No one other than the intended recipient of the email can read the emails you send or access sensitive attachments you send across.
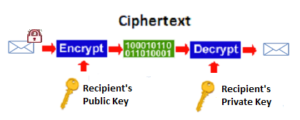
The private and public keys are an integral part of S/MIME:
- When you send an email, it’s encrypted by the recipient’s public key.
- When the email arrives at the recipient, it’s decrypted using the private key.
Digital Signatures
Digital signatures provide crucial security and validate the sender’s identity so that you can be sure they are whom they claim to be.
Likewise, S/MIME allows you to sign your emails, proving that you are the legitimate sender. The private key will create a unique Digital Signature (Hash Code) for each email you send. Each time you send an email, your private key will apply a digital signature and encrypt the hash code with a private key. The public key that is sent along with the email will verify your identity.
When the recipient opens the email you sent, the recipient uses the public key to decrypt the hash code and will confirm your digital signature (hash Code) is authentic. This signature assures the recipient that you are the legitimate sender of the email and also confirms your identity.
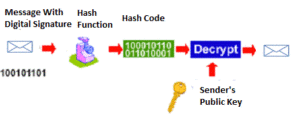
S/MIME plays a key role in email security by using digital signatures and email encryption. When you receive a message, you can verify that the sender is legitimate and that no one else has accessed your email to modify the data.
How Does S/MIME Enrolment Work
S/MIME enrolment requires a trusted Certification Authority (CA) to provide key roles for S/MIME enrolment:
Issue S/MIME Certificate from Trusted Certificate Authority (CA)
A trusted Certificate Authority (CA) generates S/MIME certificates for binding S/MIME public keys to their owners. Each S/MIME certificate the Certificate Authority issues uniquely identifies the owner. It contains the owner’s name, the expiration dates (or validity dates) of the certificate, the S/MIME public key of the certificate owner, which is used for email signing and encryption, and the digital signature of the issuing CA that issues the digital certificate to the certificate owner.
The CA attests to the validity of the S/MIME certificate—to prove to others that the owner of the certificate is whom they say they are. To do this, the CA certifies the identity of the certificate owner by applying its own digital signature. The CAs digital signature authenticates itself as the issuer of the certificate, verifies that the certificate has not been altered since it was signed, and binds it to the signing activity.
Digital certificate content

CA is required to issue S/MIME certificate for each user in your organization and each S/MIME includes a S/MIME certificate (public key) and a private key for the purposes of Email signing and encryption.
Publish S/MIME certificate (Public Key) to LDAP
To allow SMIME public key distribution for email encryption, CA publishes S/MIME certificate (public key) to LDAP directory such as Microsoft Active Directory. This allows users or employees to search and retrieve the recipient’s public key for email encryption. Email clients such as Outlook will automatically search and retrieve the recipient S/MIME certificate (public key) from the LDAP directory.
Escrow S/MIME Private Key
To facilitate SMIME private key recovery, SMIME private keys are escrowed on CA. to allow SMIME private key recovery. When users lose their private keys, any email information that was encrypted with the corresponding public key is no longer accessible.
Deliver SMIME certificate (Public Key) and Private Key to users
After you get your S/MIME public key (S/MIME certificate) and private key usually in PKCS12 format from CA, you will need to install and enable it in your email client before you can use S/MIME.
Which Email clients support S/MIME?
Following email clients that support S/MIME:
- Apple Mail
- Gmail
- iPhone iOS Mail
- Android Samsung Email and Outlook Email
- Microsoft Outlook and Outlook on the Web
- Mozilla Thunderbird
It is very easy to distinguish what a trusted email experience looks like within Microsoft Outlook. The following example demonstrated S/MIME in Microsoft Outlook:
There are three primary trust indicators in the Outlook
1. The red ribbon, which shows that this email is signed.
By contrast, in the untrusted email experience, an unsigned and unencrypted email does not display a ribbon or a padlock. In this case, it is technically possible for the from address to be spoofed.
When the e-mail is received, the recipient’s e-mail client displays a signed icon that shows that the received email message is digitally signed with a red ribbon.

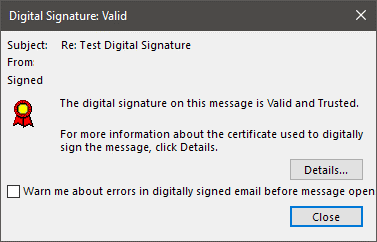
2. Verify the identity of the sender
Outlook Digital Signature validation dialog box flagged digital signing as valid and from a trusted sender.
3. The padlock icon, which shows that the email is encrypted.
When the email received is encrypted, Outlook displays a padlock icon indicating that the message has been encrypted. Outlook automatically handles the decryption when the e-mail is opened.
What are the benefits of S/MIME?
We will explain why you should use S/MIME to secure your emails.
S/MIME Protects Against Phishing Email Attacks
Sending fraudulent emails that trick the recipient into performing a task, usually sending money or passing on credentials, is a common method of phishing.
It is extremely difficult to train employees to detect and avoid phishing attacks and It is getting difficult to differentiate between fake and legitimate emails. It’s crucial to confirm the senders of emails due to the rise in phishing attacks.
By using S/MIME digital signature to verify the sender’s identity, users or employees will be able to distinguish between legitimate emails and scammers.
S/MIME allows you to:
- Digitally signing your emails to prove that you are the genuine sender.
- Protect from email Phishing
S/MIME Secures Email communication
We send important information via email every day. Trade secret, customer information, financial reports, etc. We don’t always realize we’re talking about confidential information.
When you send an email containing confidential information, you can be confident that S/MIME will secure the contents and ensure that only the intended recipient can decrypt the email and access its contents.
SMIME offers end-to-end email encryption because the email was encrypted from the start and only decrypted at the receiver’s end, S/MIME provides assurance that the email’s contents were not read by anyone and ensure that only the intended recipient can read the email’s contents. With S/MIME encryption, your sensitive data remains confidential, even if an attacker gets their hands on your emails.
S/MIME allows you to:
- Encrypt the email messages you send.
- Prevent the disclosure of sensitive information.
- Protect your organization, employees, and clients’ data.
How to Start With S/MIME Implementation
When it comes to implementing S/MIME, deployment is the most difficult challenge. Everywhere users or employees read email, from mobile devices and laptops, the same SMIME public/private key pair must be installed across multiple devices making user or employee burden higher to manually install and configure S/MIME on multiple devices.
Some of the biggest challenges is managing S/MIME keys and configuring SMIME on users’ email client, with a large number of manual steps from enrolling/distributing SMIME to users, installing S/MIME on email client to manually recover S/MIME keys from Certificate Authority. Therefore, making it is very difficult for organizations to scale without IT and employee support overhead.
Fortunately, S/MIME deployment can be automated and centrally managed S/MIME keys capabilities to streamline the implementation of the S/MIME process more straightforward across organizations
By automating S/MIME delivery, users can avoid having to manually install and configure each mail client and device they want to use with SMIME. S/MIME keys are created, stored, and managed from a centralized management workflow. S/MIME keys are automatically installed on user devices to allow users and employees to use S/MIME on email clients that were centrally created for them.
S/MIME automation provides a capability to provision S/MIME keys in a secure way and reprovision or recover the same S/MIME keys to multiple user devices. This help to alleviate the employee burden of requiring to install and manage S/MIME on multiple devices. In case of loss of S/MIME private keys, centrally manage S/MIME keys enables organizations to recover employees’ S/MIME keys Therefore allowing an organization to restore access to encrypted email data.
Wrapping up
When looking for a way to secure email that will protect organizations’ sensitive and confidential information from data leaks, S/MIME with digital signature and encryption can help.
S/MIME is an effective email encryption standard that protects your email data, secures your email and lets your recipients know that your email domain can be trusted.
By using S/MIME, organizations can be sure that all emails send and received will be encrypted and secure and that no one could not access sensitive information. Along with S/MIME automation capabilities that make it easier for organizations to scale secure email across their employees or users.
Considering the security features S/MIME has to offer, it is time to consider implementing S/MIME in your organization. Reach out to Netrust consultants at sales@netrust.net or contact us via our website today.
Follow us on LinkedIn for the latest happenings/updates.


