Securing PDFs with Digital Signatures
The Portable Document Format (PDF), an acronym that I dare say that everyone is familiar with, has become an integral part of everyday life for most employees and employers alike. Used and preferred as it operates across multiple Operating Systems (OS) e.g. Windows & Mac. , it is the de-facto standard for electronic documents ranging from casual use such as, storing images of your pet to professional use like one’s payslip and even title deeds in banks and organizations alike.
Digital Signatures

Digital Signatures are a common way to protect important documents to help guarantee the integrity of a document while allowing the signer of the document to remain verifiable.
A digital signature is generated using mathematical algorithms to generate a unique digital fingerprint of the document that is signed by the signer using the signer’s private key. This digital signature is then stored within the PDF document for future reference alongside the signer’s certificate, also known as the signer’s identity.
On receiving the document, when the recipient wants to determine the authenticity of the document for example a title deed – the document’s unique digital fingerprint is then computed on the recipient’s computer and matched against the stored PDF’s digital signature’s unique digital fingerprint. If the unique digital fingerprint matches, then the authenticity of the document is confirmed.
As complicated as this might sound, PDF defines a standard for this to be processed automatically. Widely available clients/applications such as Adobe Reader and Foxit Reader natively support the verification of digital signatures. Verifying the digital signature would be as simple as opening a PDF document and letting the Adobe Reader client/application inform you of the verification status of the document.
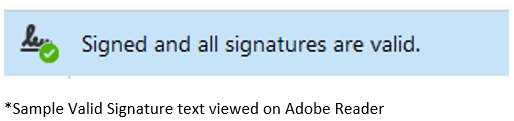
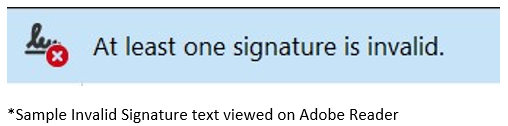
How would we validate a Signer’s Digital Identity (aka Digital Certificates)
Before we can start utilizing digital signatures to protect our documents. It is important to first get a trusted third party that can ascertain your identity. Certification Authorities play a major role in validating the identity of the entities. Upon successfully validating the identity of the user. A digital certificate is issued to an entity that represents the user’s identity.
Digital signature produced using a Netrust digital certificate provides legal presumption with our secure electronic signature (SES). It would be good to note that digital certificates are not limited to only users, organizations too can procure certificates for backend processing purposes or to sign as organizations. Signing as an organization would typically be used on documents that require proof of authenticity.
It is important to note that not all digital certificates have the same legal presumption in a court of law. Netrust is an accredited Certification Authority in Singapore that is audited by IMDA and documents signed by Netrust’s digital certificates have a legal presumption in Singapore’s Court of Law. This is because we comply with the Electronic Transaction Act (ETA) and perform the highest level of verification before a digital ID is issued. Find out more information relating to certificates by checking out nSignBasic.
Adobe Approved Trust List (AATL) for Digital Identity (aka Digital Certificates)
All Certification Authority will be able to produce a digital certificate for use with signing. However not all Certification Authority will be trusted by default within the Adobe Reader or Foxit Reader client.
Certification Authorities like Netrust have to go through a rigorous process to qualify for this program. Details would include ensuring that the Certification Authority’s service and credentials meet the assurance level imposed by Adobe’s AATL technical requirements.
In the event, that a recipient receives a digitally signed document whose signer’s digital identity (or digital certificate) is not from an AATL trusted Certification Authority (for example Netrust). On opening the signed document, they will be presented with the following warning in the screen capture below.
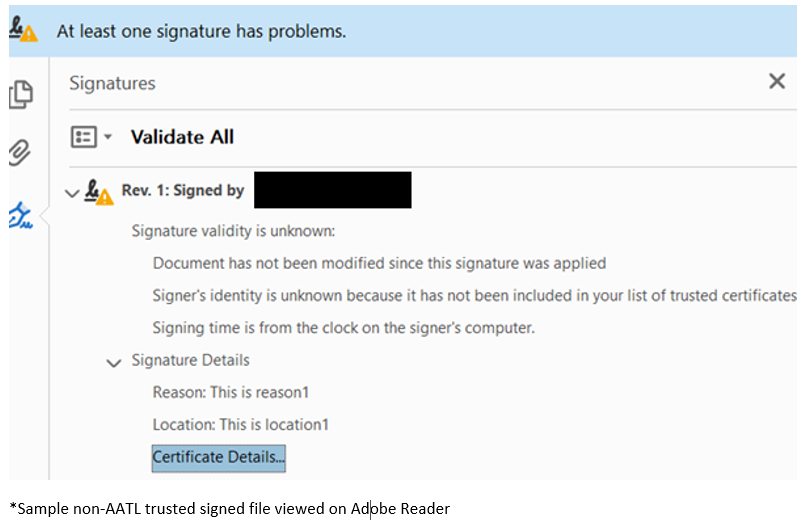
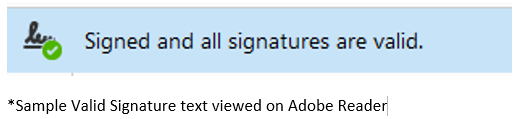
This effectively means that the referee or Certification Authority in this case is not trusted by Adobe and recipients of the document would have to manually trust the Certificate Authority in order to get the familiar green tick as seen below.
Revocation Data for a Certificate
Revocation checks performed on a digital certificate is pivotal, as it represents the identity of a signer. Any digital certificate can be checked in one of two ways, through a Certificate Revocation List (CRL) also known as a blacklist. Or an Online Certificate Status Protocol (OCSP) response.
A CRL or a blacklist, as the name implies – keeps track of all compromised digital certificates.
The OCSP response, on the other hand, provides a snapshot in time of the status of a certificate.
In either scenario, if a digital certificate is blacklisted either via the CRL or OCSP the state of the certificate would be revoked, implying that the digital certificate is not valid for use any further. After a revocation, any further attempts to sign using a digital certificate of revoked status will be rejected as revocation checks are performed at the point of signing.
Entities are also expected to inform the Certification Authority in the event they suspect that their private key has been compromised/leaked. Users requiring a new digital certificate would then have to request a new certificate.
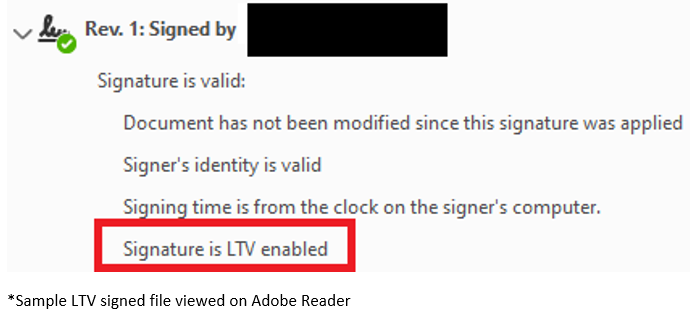
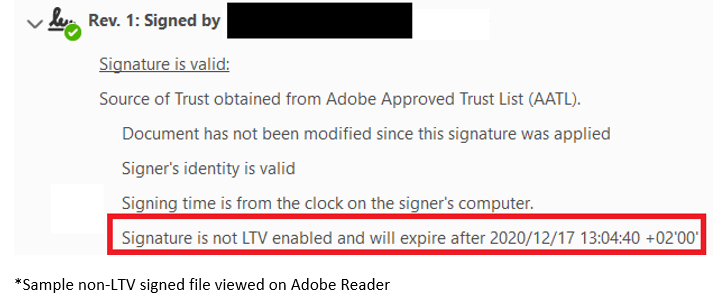
Long-Term Validation (LTV)
As referenced in the previous blogpost on consuming the Sign with SingPass service with nSignSG, it is imperative for recipients of the document that assurance of the signed documents is valid at the point of signing.
In the event, that LTV is not enabled for a digital signature, there is a possibility that at the point of time in signing, the signer’s identity (aka digital certificate) is revoked.
Hence, for the added assurance on the signer’s identity, who at the point of time in signing – is still in control of their keys. Revocation checks are performed using the revocation mechanism mentioned previously to ensure that the digital certificates are not revoked.
Upon completion of the revocation checks for the digital certificate, the revocation data is then embedded within the document as part of the digital signature.
nSign Digital Signing Solution
Digital signatures might sound complicated, but it does not have to be. Generating digital signatures can be automated and easily integrated with Netrust’s nSignCore Signing Solution.
nSignCore integrates easily with REST API to existing backend applications to enable your application to create digital signatures. If you’re located in Singapore, nSignCore can enable your application to consume the Sign with SingPass feature alongside a myriad of other functionalities. It can also be tailored to specific use-cases e.g. backend signing and desktop signing with USB crypto tokens, physical HSM appliances and even cloud-based HSMs by commercial cloud providers.
Wondering how nSignCore would integrate with your business application? Take a look at our FREE service, nSignSG which provides end-users with the ability to create digital signatures using the Sign with SingPass eService and SingPass Mobile Application! nSignSG is powered by our own nSignCore under the hood.
Should you require a signing solution with little to no integration, nSignHub might be the solution you are looking for. nSignHub allows for a signing workflow solution without a business application. Take a look at this article, e-Signature workflows made easy written by Yu Jie outlining the benefits of using nSignHub.
Should you have any questions regarding nSignBasic, nSignCore, nSignSG, nSignHub or questions in general, do reach out to us at sales@netrust.net.
Follow us on LinkedIn for the latest happenings/updates.



